- 1 Government at Scripps Green before Ransomware Operations
- 2 Scripps Green Cyber Crime Operation
- 3 The FBI Did Not Want to Have a Meeting
- 4 Government Lies
- 5 Scripps Cyber Cime and More
- 6 Russians Charged for Providing TrickBot (Not the Whole Story)
- 7 Russians Indicted (Not Like They’ll Ever Be Questioned)
- 8 This Was All Staged By American Government Infiltrators
- 9 Discovery of Scripps Ransomware Operation Before it Went Live
- 10 My Departure from the United States
- 11 Non-Technical Reference Demonstrating I Was Writing About Attack Before It Occurred
- 12 The FBI Response and other Federal Law Enforcement Agencies
- 13 May 1, 2021, Go Live Date: Ransomware Attack on Scripps in San Diego, California
- 14 Suspects Starter List Involved in Scripps Ransomware Operation and Data Heist
- 15 On-Site Criminals Involved in Ransomware Heists
- 16 Feed post
Government at Scripps Green before Ransomware Operations
Scripps Green Cyber Crime Operation
I was aware of a cybercrime operation being staged by September 2020. At the time, I was not aware that the government was staging it. It took a long time for me to figure out what was happening. It took years of being terrorized and reviewing and re-reviewing events and evidence.
Ask yourself how is it that I knew about the Scripps ransomware operation a week before it occurred and was writing about months before it went live including the week before. Ask yourself why the FBI did nothing to stop the operation.
The FBI Did Not Want to Have a Meeting
I sought a meeting with the FBI multiple times and it was denied. I was given the run around while I was being terrorized, forced out of multiple homes, at my job, and outside my office, then illegally detained, subjected to a smear campaign, stalked at my home, intimidated, unlawfully held, chased, harassed and threatened at this time (all at the direction of government personnel). It was a nightmare carefully orchestrated by special operations personnel. This only became worse over time. It was a complete nightmare by the time I took this photo.
I was speaking to friends telling them about how Pegasus had been dropped on my phone while living in Mexico. I had this conversation the day before. United States government special operations personnel have a gaslighting tactic. They have a massive lurker team listening to targets and what they do as part of their gaslighting and harassment tactics are to present to the target evidence of lurking (eavesdropping) and physical surveillance.
I have hundreds of examples. I was telling someone about a planned job at Scripps, staged by the cybercriminals, and Pegasus, and this was mirrored back to me the next day or two. This was the reason I took the photo. 187. 1 (800) 734-3878 is a signature for the personnel involved. It is these people Exclusive: Inside the Military’s Secret Undercover Army who are involved at least in part with these operations.

Government Lies
- Hollywood Presbyterian (possible) -attributed to Iranians.
- City of San Diego (aborted)
- Scripps Hospitals (San Diego) -attributed to Russians (settlement)
Scripps Cyber Cime and More
The Hollywood Presbyterian operation was less than a mile from one of my former homes which was adjacent to a house tied to Japanese Yakuza and likely tied to Koreans. The occupants were engaged in cyber crimes and identity theft, and thefts of items to support these activities. I suspect that they are tied to the Hollywood Presbyterian job as part of the onsite reconnaissance team. I am uncertain.
Russians Charged for Providing TrickBot (Not the Whole Story)
How convenient to charge a few Russians who will never face any justice for providing the software as they will never be extradited. The truth is United States government covert operatives infiltrated various threat groups in leadership positions. They staged a number of criminal activities and provided various services to the Sinaloa Cartel, the Asian OCGs and Bloods involved in various aspects of these jobs. There were onsite reconnaissance teams at these locations.
I reported it to law enforcement. I reported it to friends. I reported it several months before it went live and had files on my computer about the same. The government did nothing and worse. They wanted this job to happen so they could further ingratiate themselves with various threat groups. They made it happen. I fled or more appropriately was steered to Europe a few months after it went live. I was to be used by Europeans to lure out these globally connected threat groups who were quite unhappy with me for discovering multiple cybercrime operations (one aborted) and this Scripps Operation that went ahead with cover operatives hands guiding it.
These have led to the unprecedented results by the JCODE team. This is all Special Projects or more likely Special Activities Division meets the Defense Clandestine Service activities.
Russians Indicted (Not Like They’ll Ever Be Questioned)
This Was All Staged By American Government Infiltrators
Discovery of Scripps Ransomware Operation Before it Went Live
Early September 2020, I became aware of the Scripps Ransomware Operation which went live May 1, 2021. This attack resulted in a $113 million loss and was fully preventable were it not for corruption and ineptitude.
Yes, I knew about it when the ransomware gang was doing reconnaissance several months before and I knew who was involved. Corrupt law enforcement acted at the local level who serve the Sinaloa Cartel to silence me and create a false narrative. Again it was all about poisoning the well with me from July 2020 forward. These are common tactics. (For example, the LAPD has been the focus of recent California DOJ investigations for falsified field contact entries involving numbers of citizens). Anyway, the Sinaloa Cartel mobilized its partners as it was the Sinaloa Cartel who was backing the ransomware gang and providing other operational assistance.
My Departure from the United States
I had to leave the country due to attempts to silence me from getting me into custody on bogus charges, intimidating me and those close to me, persistent threats, and harassment as promised in their threat note, and multiple deployments of corrupt personnel to foster a discredit narrative and poison the well to prevent task force involvement and my protection
As of today, February 22, 2022 nothing has been done, because those involved have remained protected criminals due to law enforcement corruption.
Duke | Early September 2020, I had identified several insiders employed at Scripps Hospitals as being involved in the operation. They were also involved in the early stage reconnaissance at the city of San Diego which they planned to ransom, but the job was aborted because I began unraveling their criminal network. I know for a fact and have evidence as they wanted me to obtain the password for the City of San Diego Barracuda device and had told meet them in Lennox Park in South Central Los Angeles. Same ransomware gang and same tactics.
I have posted a small portion of the evidence, to begin with, and one can look at my draft affidavit in the Key Docs submenu on this website to view a very small mostly non-technical portion of it and events related to it. The ransomware gang had the same game plan at each site: employ insiders, engage in comprehensive reconnaissance and planning before the attack. Use multiple infection vectors. Engage in operations at night to supplement the insider day team: janitors and security guards. I was in a position to know. I worked very late and besides those involved was the only employee working late in an 18 story building with enough common sense and technical knowledge to see what was going on and begin digging into it.
As to how I knew they were working Scripps, I will not disclose in this post, but you can discern by reading below, I knew about the ransomware heists ahead of time.
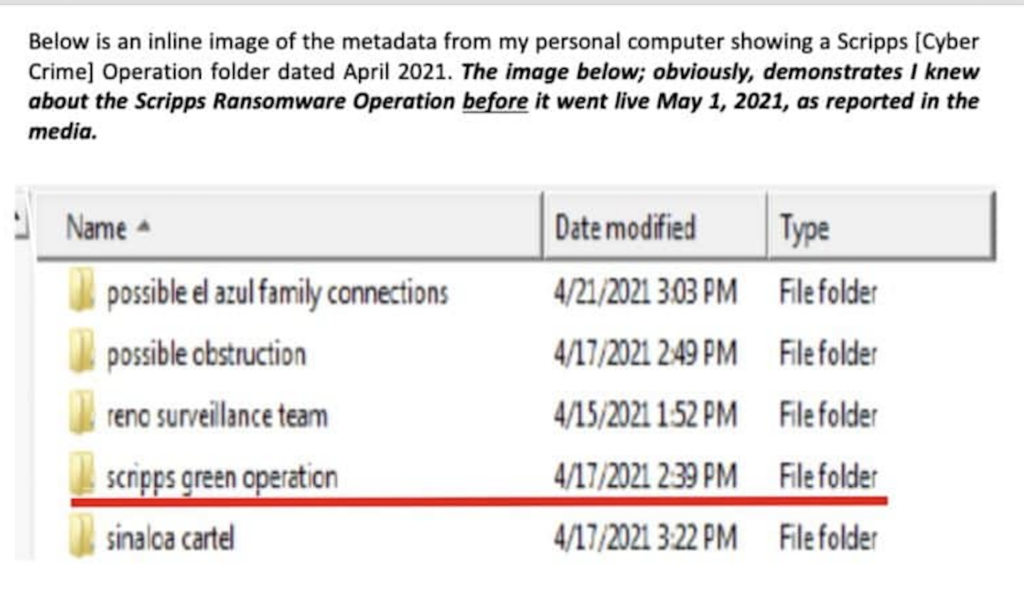
Non-Technical Reference Demonstrating I Was Writing About Attack Before It Occurred
Duke | The below is an image of a portion of my computer file system. The metadata shows you that I was writing about the Scripps Ransomware Operation (Scripps Green Operation) on April 17, 2021, and the Sinaloa Cartel. The attack went live about 2 weeks later on May 1, 2021. Am I psychic? No. Of course not.

The FBI Response and other Federal Law Enforcement Agencies
The FBI has done zero nor even accepted evidence or viewed the evidence. Nothing. (My story is about to be another debacle added to the FBI’s lists of embarrassments like that involving the United States gymnasts and the FBI’s mishandling of that case: Slow to investigate or do not investigate, quick to engage in disbelief, lost in bureaucracy, failures to follow up, and putting witnesses at risk -and in this instance victims at the mercy of ransomware gangs to the tune of 113 million dollars. Same story and different case. Anyone reading this post that wants to send this post to Justice Department officials from the FBI Ransomware Taskforce, Organized Crime, or Public Corruption, please do. Perhaps Secret Service (I believe they handle some cyber intrusion of a financial nature and this gang is very active) – and HSI should have an interest because I know about the gang’s interests in critical infrastructure data, please do.
May 1, 2021, Go Live Date: Ransomware Attack on Scripps in San Diego, California
The delay in the ransomware operation’s go-live date to May 1, 2021, was likely due to the issues I posed for the operation. The attack team was aware I knew about it, and that I was attempting to obtain federal protection. This is why they took extraordinary steps to silence me using its most effective weapon: corruption. I fled from California under threat and had sequestered in the home of an attorney far from California. I was supposed to leave the country on April 30, 2021, the day before the Scripps operation went live. The operation still went live on May 1, 2021. Coincidence?
Suspects Starter List Involved in Scripps Ransomware Operation and Data Heist
- Some contract security guards.
- A white male in an old El Camino parked outside overnight scanning or intruding. I have his license plate:
- Members of the hospital staff, I will not identify here. Asian male
- A cartel maintenance proxy was responsible for power washing the front of Scripps Green. Halcon (not kidding)
- This Pegasus wrapped van (part of a larger PsyOP operation) as I had been stating on my intruded phone they had deployed Pegasus when living in Mexico and something with similar functionality in the United States. This is a sophisticated group with some gaslighting techniques blended with PsyOp to intimidate targets. It is what one might expect from special operations personnel serving the Sinaloa Cartel along with hackers.
- Donald (Filipino male in the cafeteria). Donald, a cafeteria worker.
- Another female cafeteria worker onsite at the same time as Donald will be able to provide some information.
- Asian male in Imaging at Scripps Green. Late 20s taller and thin.
- Blood suspects
- American Airlines flight manifest, Dallas to San Diego. Approximately 30s, white male.
- Female insider employee, I know about.
I will disclose all and clarify and detail the above information if provided protection.
On-Site Criminals Involved in Ransomware Heists
FBI Ransomware Task Force: Look for employees with ties to Los Angeles and San Diego and ties to PIRUs/ Bloods and Asian street gangs south into Orange County and San Diego. Male and female: 20s and 30s. Again, you should also contact me and provide protection.
I have no doubts they would have obfuscated the attack with foreign partners by the time it went live, but I know exactly who was involved on-site at Scripps Hospitals. Not all, but enough. Employees might have quit before the attack and replacements placed back inside if needed like cafeteria worker Donald who was part of the attack team as the ransomware team was aware I had identified him. Again, I can point you to the exact people.
Feed post
Ransomware and Data Theft Team: A Lead
I was posting license plate a few years ago like below desperate for law enforcement intervention. It never came because law enforcement and intelligence were the ones puppeteering all these activities as highly placed fixers for these organizations.
The government operatives where the ones who put me in the line of fire everyday. The government created a dynamic because I uncovered its covert activities involving the fixer involving trafficking people and drugs and staging cybercrime activities.
The government was sending all these people in and some of the plates are intelligence operatives. I was a law enforcement puppet and decoy for the government infiltrators who unleashed a global terror campaign after I began reporting on their covert activities. I was originally made to believe they were corrupt government personnel. This was a a false flag operation. The Asians were being sent in by the American “fixers” to do reconnaissance.
The Original Post Follows
There are license plates of suspects in a draft affidavit I posted a few months ago on LinkedIn. I have a lot more.
I intentionally left a lot out of that draft affidavit and other TIPs emails because it was best to disclose it in a meeting due to man-in-the-middle activity. I did not want to jeopardize any potential investigation. However, the FBI, DEA and every agency refused to assist through today (to cover black operations) and use me.
However, this forum will have to suffice given the TCO, OCGs and other enablers attached to the criminal operations are above the law as evidenced by United States law enforcement doing nothing but for the cartel law enforcement lackeys engaging in obstruction.
Nevertheless here is another lead: an Asian female driving a Volvo X370, California license plate 7MOC403 or TMOC403 or something similar.
Rotating Team Outside Government Building
Government Puppets
The license plate frame was San Francisco Van Ness. She was parked outside the City of San Diego building at 1200 Third Avenue. End of July 2020. I am uncertain as to her role.
The attack team included a rotating team of Asians that would park in the same spot outside my law enforcement office and the IT offices for all of San Diego. At least during June and July 2020.
I quietly dubbed the parking spot outside my office, “Parking for Asians.”
Keep in mind those involved include some individuals skilled in obfuscation and deception, online and offline, from doppelgängers to other decoys and more.
#ODNI #Europol #DHS #Interpol #FBI #DEA #NCIS #CID #ODNI #OSCE #InsiderThreats #NationalSecurity #Corruption
#OrganizedCrime #InsiderThreat #USSenate #BKA #BND #FedPol #DataTheft
All suspects are innocent unless convicted in a court of law.Activate to view larger image,
So by early summer 2020, I was aware of an active operation with onsite attackers engaged in recon and could identify them. They were targeting the City of San Diego and intrusion and lateral movement had already occured. I was a targeted vector. I knew a lot by that point in time. I had reported to the day private security supervisor that I had witnessed an Asian male tailgate into our (in)secure underground parking lot then jump into the elevator. I had never seen him before.
The private guard quickly dismissed it, and suggested it might be a building contractor. Whether he was a building contractor or not this fits into the attack teams methods. This private guard probably knew nothing about social engineering, tailgating, reconnaissance or ransomware and data theft teams using insiders etc. rendering my report meaningless. More on all this in another post and why a “building contractor” insomuch one might have been involved would have been another good insider for the data theft portion of the job.…see more
MessagingYou are on the messaging overlay. Press enter to open the list of conversations.Compose messageYou are on the messaging overlay. Press enter to open the list of conversations.https://li.protechts.net/index.html?ts=1708416308036&r_id=AAYRy6q%2BNvDo1lf8UZVkpA%3D%3D&app_id=PXdOjV695v&uc=scraping&d_id=4a10e6a3a08d0b822460ecc870630f2cd39312136067ce6a517deb86f34833cb
Ransomware and Data Theft Team: A Lead
I was posting license plate a few years ago like below desperate for law enforcement intervention. It never came because law enforcement and intelligence were the ones puppeteering all these activities as highly placed fixers for these organizations.
The government operatives where the ones who put me in the line of fire everyday. The government created a dynamic because I uncovered its covert activities involving the fixer involving trafficking people and drugs and staging cybercrime activities.
The government was sending all these people in and some of the plates are intelligence operatives. I was a law enforcement puppet and decoy for the government infiltrators who unleashed a global terror campaign after I began reporting on their covert activities. I was originally made to believe they were corrupt government personnel. This was a a false flag operation. The Asians were being sent in by the American “fixers” to do reconnaissance.
The Original Post Follows
There are license plates of suspects in a draft affidavit I posted a few months ago on LinkedIn. I have a lot more.
I intentionally left a lot out of that draft affidavit and other TIPs emails because it was best to disclose it in a meeting due to man-in-the-middle activity. I did not want to jeopardize any potential investigation. However, the FBI, DEA and every agency refused to assist through today (to cover black operations) and use me.
However, this forum will have to suffice given the TCO, OCGs and other enablers attached to the criminal operations are above the law as evidenced by United States law enforcement doing nothing but for the cartel law enforcement lackeys engaging in obstruction.
Nevertheless here is another lead: an Asian female driving a Volvo X370, California license plate 7MOC403 or TMOC403 or something similar.
Rotating Team Outside Government Building
Government Puppets
The license plate frame was San Francisco Van Ness. She was parked outside the City of San Diego building at 1200 Third Avenue. End of July 2020. I am uncertain as to her role.
The attack team included a rotating team of Asians that would park in the same spot outside my law enforcement office and the IT offices for all of San Diego. At least during June and July 2020.
I quietly dubbed the parking spot outside my office, “Parking for Asians.”
Keep in mind those involved include some individuals skilled in obfuscation and deception, online and offline, from doppelgängers to other decoys and more.
#ODNI#Europol#DHS#Interpol#FBI#DEA#NCIS#CID#ODNI#OSCE#InsiderThreats#NationalSecurity#Corruption
#OrganizedCrime#InsiderThreat#USSenate#BKA#BND#FedPol#DataTheft
All suspects are innocent unless convicted in a court of law.
So by early summer 2020, I was aware of an active operation with onsite attackers engaged in recon and could identify them. They were targeting the City of San Diego and intrusion and lateral movement had already occured. I was a targeted vector. I knew a lot by that point in time. I had reported to the day private security supervisor that I had witnessed an Asian male tailgate into our (in)secure underground parking lot then jump into the elevator. I had never seen him before.
The private guard quickly dismissed it, and suggested it might be a building contractor. Whether he was a building contractor or not this fits into the attack teams methods. This private guard probably knew nothing about social engineering, tailgating, reconnaissance or ransomware and data theft teams using insiders etc. rendering my report meaningless. More on all this in another post and why a “building contractor” insomuch one might have been involved would have been another good insider for the data theft portion of the job.


