Sinaloa Cartel is a Doormat for Spies
The Sinaloa cartel is a doormat for United States spies. The spies provide fixer services in exchange for introduction and access to its global network. Fixer services are crimes and of themselves drug trafficking, human smuggling, witness intimidation, and obstruction to hide these criminal activities undertaken in the course of covert operations. The DEA and FBI benefit off these relationships and the activities are classified and if someone outside this dirty cabal uncovers these activities they engage in more dirty operations and compartmentalize it (despite the fact they are no longer classified operations as they have been uncovered).
The Sinaloa cartel is a valuable resource. So whatever the cost might be a DEA agent, border patrol agent killed by guns filtered to the Sinaloa Cartel (Operation Fast and Furious), or an investigator at a third-rate agency who discovers covert operations involving special operations personnel (me) -the lengths to which the United States will go to protect this relationship so far have no limits.
The operatives are like predators who feed intelligence to other personnel who wait to pick them off via means that can not be attributed to the bottom feeder operatives buddied up with the cartel.
Sinaloa Cartel
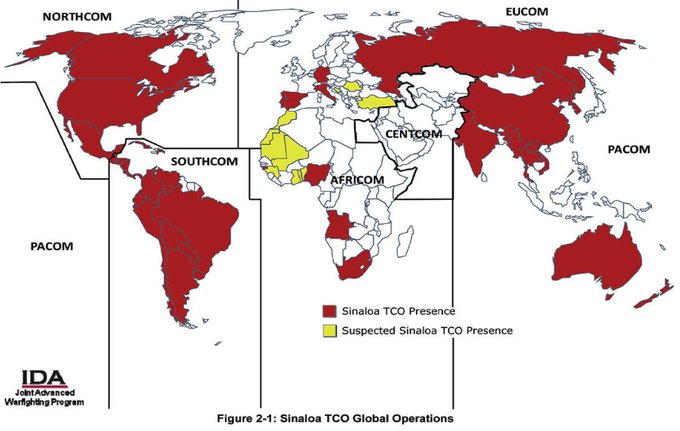
Government Personnel Do Dumb Things
The government operatives involved developed and executed a layered and completely unnecessary plan to protect covert operations. Rather than pulling me aside, they decided to implement a resource-intensive plan that centered around deploying COINTELPRO -like tactics of harassment, intimidation, and smear campaigns, and worse while attributing it all to the Sinaloa Cartel and Bloods and themselves as corrupt fixers for the cartel. This was done for multiple reasons.
1. prevent exposure of covert operations.
You can check out my web page on deception. On that page, there is a formerly classified but now publicized manual on covert online operations. I think people don’t know even how to interpret that document. The primer is about covert online (intimidation, harassment, and fear-mongering) which is exactly what the government personnel did supplemented with an offline campaign that has gone on 24/7.
So the government operatives had covert activities that were exposed and created a plan using covert means to attempt to covert it up. You might as well substitute in the word illegal for covert. So I discovered government personnel engaged in illegal operations, and they responded by engaging in a campaign that included illegal (covert) activities to harass me 24/7. The online covert cyberwarfare campaign is only a part of it. They constructed a terror campaign targeting my digital world and when not online the physical world. They basically attempt to break and bury people as part of their dirty operations as they had promised in the threat note which you can view by clicking on those words.
2. Further Ingratiate the operatives with cartels and mafias
3. Most importantly perhaps, was to terrorize and control me so that I would flee across the United States and eventually Europe. Special Operations personnel designed the plan so that they could call out local threat group members and associates wherever I went. I was forced and terrorized across several countries and 38 states in the United States from 2020 through 2024. This is how it worked: I would be in Mexico, and they told the cartel members to go out and watch me and follow me around or post up outside my house. I would go to San Diego, and they would call out San Diego crews, San Francisco would be the San Francisco crews, Dallas and Dallas, and in Berlin, it would be Berlin and thousands of others on “vacation” or in Vienna Austria, the local networks in Vienna.
First, as you look at the findings, because of the over-focus on mission accomplishment, and employment, it came to the leadership detriment of discipline and accountability. Richard Clarke SOCOM commander.
Cognitive Warfare

The Methods to Terrorize
This is not a manual about deception. The title is in part deception. It is a blueprint for creating covert online terror campaigns.
The clandestine or covert operatives devised a plan which the cartel signed off on that involved using special warfare tools and techniques and personnel along with the threat group members to execute there terror /illumination plan. It was necessary to put me in a constant flight or fight response by terrorizing me, ensuring no law enforcement would come to my aid (and when they did come use them against me) at staged settings and illegal stops. The job of the cartel associates and other mafias was to gaslight me using carefully designed influence operation techniques. Meanwhile, the SOCOM team engaged in a constant monopolization of my sense of perception using various classified tools to threaten, and fear monger me.
The tools are cyber warfare, psychological warfare, and electronic warfare tools which were utilized by a 24/7 team assigned to harass and intimidate me. The cartels and mafias thought it was rogue/corrupt government personnel providing fixer services i.e. witness intimidation and obstruction of justice. However, the truth was it was the government personnel covering up its illegal covert activities while moving forward with its Mission (in part to combat transnational organized criminal networks and state actors) using me as the bait to illuminate threat groups. It would be like the government “fixers” highly placed calling their regional people, and saying we have a rat (Christian Duke) coming into San Francisco, or Berlin, or Belgium or New York, or Tijuana, Mexico. Send all your people out to intimidate him and see what he is doing. We want you to wear this piece of clothing that would be like the a Blood gang members showing up with a red outfit on and then having a whole bunch of associates black or otherwise following me around wearing various Red gear everywhere I went along with other Blood associated gear and symbols and references like someone dressed in all red with a Compton shirt and LA hat in Berlin (this was done time and again).
are outlined the image below.
The Tools Used to Wage this Modern Warfare
Phone Line (Control, Full device access, and 24/7 Mitm)
Complete compromise of someones devices and 24/7 monitoring. This means cellular phones including the data on the phone, remote access to everything so they can delete evidence collected (which they do), full eavesdropping via MitM equipment, ability to use screen layovers, to prevent calls, of course knowledge of the phone number (can prevent and drop calls at will) and they do, as well as intercepting calls and pretending to be the person with whom you are trying to reach. For example, I called UC Berkeley regarding the need for records. My student ID is 13573206.
A woman, presumably a member of SOCOM answered the phone pretending to be the registrar, and despite having all my records with my student ID in front of me repeatedly stated, that my phone number was 1357(8)3206. This was to gaslight as part of the 187 (murder threat campaign) developed and delivered by SOCOM beginning in the summer of 2020.
Computer or Laptops
Full remote access. You do not need to be online. The ability to inject numbers and ads, etc to control any part of your online experience including intrusion software, and other MitM software the renders its own “Google” results. i.e. they are not google results. They are DOD results. They have the ability to reorient the content on any interface in real time from movie on demand screens to search result screens.
I Almost Exposed the Operations during 2022
I was posting a lot of original content on Linkedin.com and my website mcsinaloa.com. The website had significant content as did Linkedin.com.
A lot of people were viewing posts including a significant number of individuals in law enforcement at the time. I began to clearly describe something convoluted, which are influence operations (the perfect crime). I had been subjected to a massive psywar campaign over a multi-year period and began piecing together things to see that it was global operation targeting transnational organized crime and other threat actors.
Behind Enemy Lines in NaziLand with the Americans
In Germany, I was about to expose it. I was aware Germans, Americans, and other NATO and allied personnel were involved. I was weary and seriously injured from what was being done to me by the operatives who had made me a focal point of a global terror campaign to illuminate threat groups across the globe. Few things are as demented as what was done. Then I was contacted using tradecraft communications.


